In this tutorial we will learn how to install WireGuard on a Raspberry Pi 4 as a vpn server.
Install command
sudo apt update
sudo apt install wireguard -yGenerate keys for server and client
cd
mkdir wireguard
cd wireguard
wg genkey | tee pi_private.key | wg pubkey > pi_public.key
wg genkey | tee client1_private.key | wg pubkey > client1_public.key
ls
#client1_private.key client1_public.key pi_private.key pi_public.keyCopy all the keys to maybe a notepad
cat pi_private.key
#wCf0b9BGy1OV5PmBHdK7UOFsiSowUm7CA2zOlp/22WA=
cat pi_public.key
#Kf87WxgcEfL46m/TrQqZiI3ubs5/L088rdR3Z3yRgVE=
cat client1_private.key
#KLJDFmCHcAwlcn3XbZ6LG4Ab1md/EBKezvbwGTjdH1E=
cat client1_public.key
#MwUNn0tengM25oIfL3c0Asw5Kdeoit494jkSkUfyKjY=Write a wireguard server configuration file
sudo nano /etc/wireguard/wg0.confPaste this code and save the file
[Interface]
Address = 10.0.0.1/24
SaveConfig = true
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort = 37466
PrivateKey = <pi_private.key>
[Peer]
PublicKey = <client1_public.key>
AllowedIPs = 10.0.0.2/32
Replace eth0 with your raspberry pi interface name. Commonly, eth0 is the usual name for ethernet port for raspberry pi 4. If you are using Ubuntu, it usually has a different interface name such as enp14s0.
Replace <pi_private.key> with the value we got from the pi_private.key file. Do the save with <client1_public.key>.
If we apply the keys we generated, you should have this:
[Interface]
Address = 10.0.0.1/24
SaveConfig = true
PostUp = iptables -A FORWARD -i %i -j ACCEPT; iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -i %i -j ACCEPT; iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
ListenPort = 37466
PrivateKey = wCf0b9BGy1OV5PmBHdK7UOFsiSowUm7CA2zOlp/22WA=
[Peer]
PublicKey = MwUNn0tengM25oIfL3c0Asw5Kdeoit494jkSkUfyKjY=
AllowedIPs = 10.0.0.2/32Save and quit
Configure IPv4 forwarding
sudo nano /etc/sysctl.confUncomment #net.ipv4.ip_forward=1. Save and exit
net.ipv4.ip_forward=1Check if the changes applied
sudo sysctl -p
If it return ‘net.ipv4.ip_forward = 1’, then your are good to go
Configure firewall
sudo ufw allow 37466We are now ready to run our wireguard vpn server. Run this command.
wg-quick up wg0Show the status of the server
sudo wg show
interface: wg0
public key: Kf87WxgcEfL46m/TrQqZiI3ubs5/L088rdR3Z3yRgVE=
private key: (hidden)
listening port: 37466
fwmark: 0xca6c
peer: MwUNn0tengM25oIfL3c0Asw5Kdeoit494jkSkUfyKjY=
allowed ips: (none)Configure Wireguard Client (Linux)
If you are using linux computer, you can install wireguard the same way as the server
sudo apt install wireguard -yCreate a configuration file for client
sudo nano /etc/wireguard/wg0-client.confPaste this code:
[Interface]
Address = 10.0.0.2/24
PrivateKey = <client1_private.key>
DNS = 1.1.1.1
[Peer]
PublicKey = <pi_public.key>
Endpoint = <ip address>:<port number>37466
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 25Replace the value of PrivateKey and PublicKey as per the value of the keys we generated. If you use the keys we generated, you should have the same configuration below:
[Interface]
Address = 10.0.0.2/24
PrivateKey = KLJDFmCHcAwlcn3XbZ6LG4Ab1md/EBKezvbwGTjdH1E=
DNS = 1.1.1.1
[Peer]
PublicKey = Kf87WxgcEfL46m/TrQqZiI3ubs5/L088rdR3Z3yRgVE=
Endpoint = 192.168.100.100:37466
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 25The Endpoint should be the server ip. I uses local ip address for testing. But if you have domain and router properly configured for port fowarding, you can replace the endpoint to your domain name. Save the configuration file and exit.
Run wireguard client
sudo wg-quick up wg0-clientConfigure Wireguard Client (Windows)
To use wireguard vpn client in Windows, please download and install wireguard. [Click here]
Once installed, open your notepad and paste the configuration you made
[Interface]
Address = 10.0.0.2/24
PrivateKey = KLJDFmCHcAwlcn3XbZ6LG4Ab1md/EBKezvbwGTjdH1E=
DNS = 1.1.1.1
[Peer]
PublicKey = Kf87WxgcEfL46m/TrQqZiI3ubs5/L088rdR3Z3yRgVE=
Endpoint = 192.168.100.100:37466
AllowedIPs = 0.0.0.0/0, ::/0
PersistentKeepalive = 25Then file on desktop ‘File name’ as wg-client.conf and save as type ‘All Files” and click save.
Open wireguard application and import the conguration.
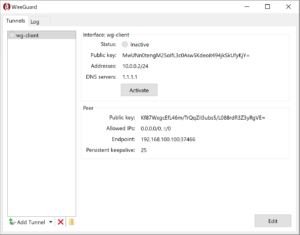
Click activate to connect vpn client to the server.
